Why the Need for this Change?
There has recently been a string of attacks on Salesforce customers, whereby hackers have been using a version of phishing called vishing (voice phishing). This is where a person makes a fraudulent phone call and tricks people into revealing sensitive information.
They tricked employees into visiting a setup page for a familiar connected app, in this case Dataloader – a commonly used app by System Administrators to import, export and update records within Salesforce, giving access to all data. However, the version of Dataloader that was downloaded, installed, and connected to Salesforce environments was actually a modified version of the app created by the hackers. It wasn’t just Salesforce access that was obtained. This version of Dataloader also gave the group access to the customer’s network, allowing attacks on other cloud services and internal systems.
Salesforce commented: “There’s no indication the issue described stems from any vulnerability inherent in our platform.” The spokesperson went on to explain that the voice calls used to trick employees “are targeted social engineering scams designed to exploit gaps in individual users’ cybersecurity awareness and best practices.”
Salesforce has also posted a blog to help users protect themselves.
Salesforce’s Answer
As a direct response to this threat, Salesforce has released a new article announcing changes, including completely removing this authentication method known as OAuth 2.0 Device Flow. To further reduce the risk of such attacks in the future, Salesforce has also removed the ability to authorise new connections to uninstalled connected apps.
To minimise disruption to existing apps in Salesforce environments:
- All previously authorised apps will continue to work as expected.
- All system administrators will receive a permission called ‘Approve Uninstalled Connected Apps’, which will bypass issues where a connection was established using a system administrator profile.
In short, we believe all current integrations should continue to work. However, after the rollout date, there will be some extra steps required to get any new connections or integrations working. Below we outline a few clear and simple steps to get that sorted.
Technical Step-by-Step Guide
It is important that these steps are completed by your System Administrator.
- In Setup, using Quick Find, search for Connected Apps OAuth Usage.
- Review the list of connected apps, specifically looking at the Actions column.
- If an app is displayed with Install, review the app and the user count.
– Clicking the number in the User Count column shows which users are using the app, when they first connected, when they last used the app, and their total use count.
– If there are old connections or inactive users, you can revoke access. - For each app that you deem to be a trusted app that displays Install, simply press the Install button, then confirm on the following screen. If you are unsure of the trustworthiness of any apps, please get in touch and we will endeavour to support you.
- If there are any apps you no longer use, or are unsure of, you can select Uninstall.
- Likewise, any apps you feel should not be there can also be blocked.
Non-Mandatory Extra Security
Salesforce provides an extra layer of security for your apps. This feature lets you decide exactly which users are allowed to make those connections.
The important thing to understand is that once this setting is enabled, all existing connections will be removed. Each connection will need to be re-established before data can flow again. While this can feel disruptive in the short-term, it offers long-term benefits by giving you tighter control and clearer visibility over who is connected to what.
If you’re unsure whether now is the right time to switch this on or you’d like support in planning the change, please get in touch.
When is this Happening?
All existing production and sandbox environments will have a phased rollout between 2nd September and 17th September.
If you need to confirm the rollout date for your specific environment, you will need to contact Salesforce Support directly.
One way to tell if your system has the patch is to ask your System Administrator to check for the permission Approve Uninstalled Connected Apps. If that is available for selection, then your environment has the latest update.
Summary
The list of organisations affected by these types of attacks keeps growing. All of this happened through social engineering, so please be wary of who you are talking to and what they are asking you to do.
Salesforce has made clear that its platform was not the cause of the attack, but it is providing ways to mitigate this issue with the latest update and its own guidance on protecting yourself.
Definitions
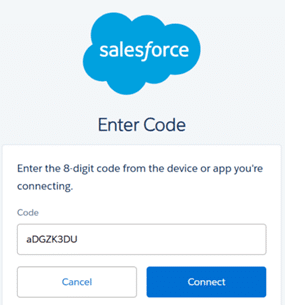
What is OAuth 2.0 Device Flow?
OAuth 2.0 Device Flow, for those who have used Salesforce’s Dataloader tool, is the process where you are prompted to enter a code to authorise the connection of Dataloader.
What is a Connected App?
Connected apps are integrations with Salesforce that allow secure access to data and other functionality. For example, pushing data in from FormAssembly, or connecting to a platform to allow single sign-on (SSO).
*Blog Photo Credit: Main image generated by Copilot for the purpose of this blog post.